Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Bitsight’s global, advanced scanning and detection capabilities provide insight into many actively exploited vulnerabilities that others just can’t touch. Explore how we do it.
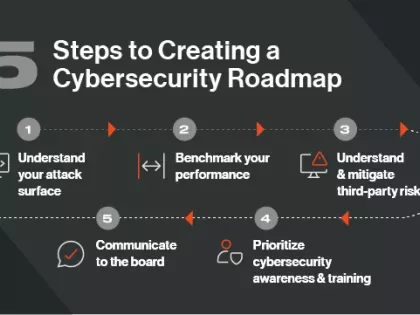
The recent rise in ransomware attacks and business-halting data breaches has made it clear that your organization must prioritize cyber security performance. But ad hoc security controls and defensive measures are not the answer. Instead, you need a strategic, risk-based approach with a cyber security road map as your guide.

Email is a well-known and widely used attack vector for malware distribution, phishing, and many other types of threats.

If you’re experiencing frustrating delays and procedural roadblocks during your vendor management process, you’re not alone. Security managers are seeing an increase in the number of third-parties integrating with their business, and Gartner reports that “60% of organizations are now working with more than 1,000 third parties”.

Cyber risk mitigation and remediation are often talked about in the same terms. But they are different. Learn how you can optimize both.

Security ratings, or cyber security ratings, are a data-driven, objective and dynamic measurement of an organization’s security performance. Thousands of organizations around the world use Bitsight Security Ratings as a tool to address a variety of critical, interconnected internal and external use cases at scale in order to enable more effective decision making throughout the global business ecosystem.

With the right mindset and governance, visibility into enterprise exposures can push priorities all the way up into the strategic realm of enterprise risk management—whilst enabling a threat informed defense posture.

For the first time, cloud security breaches and incidents are more commonplace than on-premises attacks. According to the 2021 Verizon Data Breach Investigations Report (DBIR), in 2020, 73% of cyberattacks involved cloud assets, compared to only 27% in the previous year.

Explore how CISOs can secure supply chains and meet evolving cyber regulations with strategies from our new ebook on cybersecurity resilience.

Discover why millions of smartphones worldwide are at risk due to cluttered and outdated apps. Dive into our research to learn more about this critical issue.
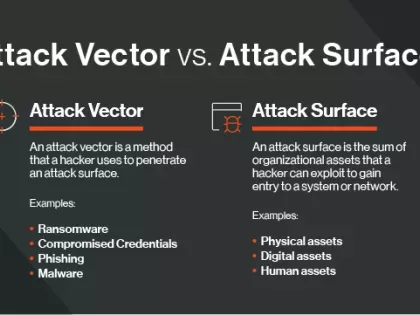
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

The vendor due diligence checklist to steer your procurement decision-making in 5 simple steps. First step: always collect the 7 basic business details.

This blog post details one of these very unique cases: `CVE-2022-44877`, an unauthenticated Command Injection issue, flagged by CISA as a Known Exploited Vulnerability (CISA KEV).

Learn the difference between third-party vs. fourth-party risk and how you can extend your risk management program to cover both.
Discover how executives and investors are aligning to fortify resilience in the face of evolving cyber threats.