Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Bitsight put together 5 tips for board members to manage cyber risk going into 2024. Read the blog to see how the modern corporate board thinks about cyber risk.

Explore recent Ivanti Secure vulnerabilities affecting SSL VPN and Network Access Control solutions. Understand the criticality, patch delays, and ongoing exploitation.

When it comes to managing hidden risk and shadow IT, our primary challenge as cybersecurity practitioners is securing the organization’s data and applications while empowering users to perform their duties efficiently.

Every year, companies spend billions of dollars on mergers and acquisitions. (The value of worldwide M&A deals in 2014 totaled $3.5 trillion.) Managing risk throughout the process is an important element of any merger, but there's one area of risk management that hasn't had the attention it deserves.

Anyone in the security space can agree that a solid cybersecurity policy goes a long way. But not everyone in your organization is a security expert. In fact, many employees may not know the first thing about firewalls or viruses—which is why cybersecurity employee training is such a critical matter.

Unearth insights to not just comply but lead in the era of NIS2, DORA, PS21/3, and emerging cyber regulations.

As more of the world’s population gains access to the internet and more and more devices come online daily, there are new and emerging cyber threats around every corner.
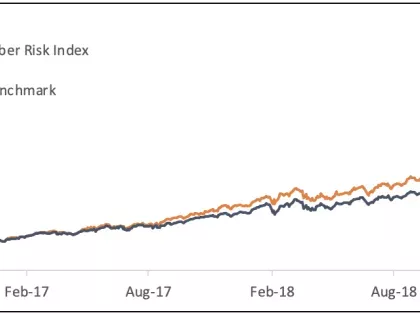
One of the biggest questions in cybersecurity now has an answer… and the implications are significant for investors, policymakers, corporate executives, and cybersecurity professionals alike.

The world of procurement has been fundamentally changed by the introduction of technology. Source-to-pay software has brought digital workflows and automation to time-consuming processes like creating RFPs, managing contracts, and remitting payments.

Using automated vendor risk assessment capabilities and tools you can eliminate manual processes, scale your VRM program, and quickly mitigate risk.

Whether you’re a security leader asked by the board to facilitate a cyber security audit, or a member of the board planning to request one, it’s crucial to know what is a cybersecurity audit & what it isn’t. You need to know precisely what is being asked for to make sure the right information is collected.

Utilizing a continuous cyber security monitoring strategy for cybersecurity can give your security team higher visibility into your threat landscape. To get the most value when investing in continuous security monitoring you first need to understand how data can be compromised. The three main ways are:

Enterprises tend to take their time with remediation efforts, despite software vulnerabilities being a top threat to organizations’ cybersecurity performance. The key to quicker fixes? Timely briefings.
.pnga340.webp?itok=_piDra7C)
Learn how to discover shadow IT with tools like network audits, CASB tools, and train staff to identify and manage hidden tech risks effectively.

Here's what policymakers can do to reduce cyber risks associated with exposed industrial control systems.