Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

This is a continuation of the series on web application security where we dive into cookie dynamics.

This blog starts with the basics as part of a series regarding operational security, such as web application headers and defenses against attacks such as cross-site scripting (XSS), cross-site request forgery (CSRF), and vulnerabilities in included libraries.

If you operate in specific sectors, cybersecurity maturity is more than a best practice, it’s a regulatory requirement. These regulations are complex and constantly changing. To help you better understand your organization's regulatory environment and the standards and controls they stipulate, let's break down key cyber compliance regulations by industry.

It's proxy season, and investors want information from companies about cyber risk. Investors are leveraging Bitsight’s data analytics to better understand the risks of their investments.
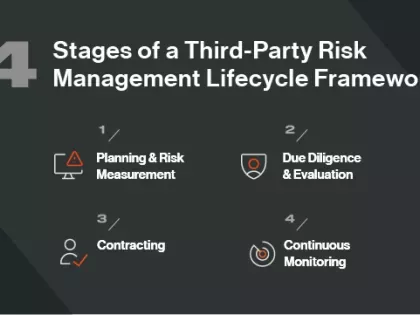
Third party risk management is trending following major data breaches affecting organizations through their vendors. But what is TPRM?

A chief information security officer (CISO)'s roles and responsibilities include many hats in the realm of cybersecurity — but they are primarily responsible for translating complex business problems into effective information security controls.

Does your organization have a cybersecurity risk remediation plan? Follow these 5 tips for crafting one.
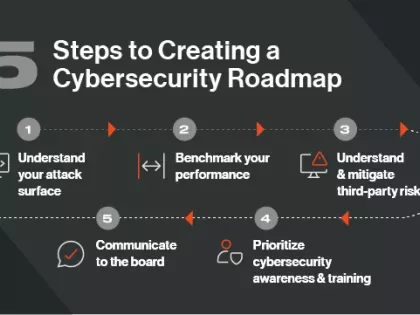
The recent rise in ransomware attacks and business-halting data breaches has made it clear that your organization must prioritize cyber security performance. But ad hoc security controls and defensive measures are not the answer. Instead, you need a strategic, risk-based approach with a cyber security road map as your guide.

Cyber risk mitigation and remediation are often talked about in the same terms. But they are different. Learn how you can optimize both.

For the first time, cloud security breaches and incidents are more commonplace than on-premises attacks. According to the 2021 Verizon Data Breach Investigations Report (DBIR), in 2020, 73% of cyberattacks involved cloud assets, compared to only 27% in the previous year.
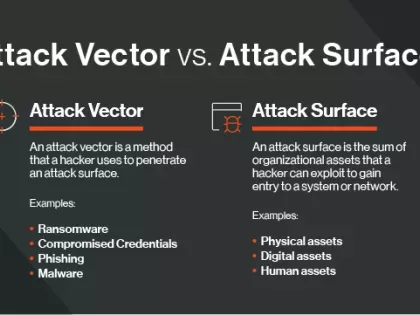
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.

Learn about the top ransomware attack vectors favored by hackers and the steps you can take to protect your organization.

What is adaptive security? Explore the benefits of this approach to cyber risk reduction and how your organization can get started.

Anyone in the security space can agree that a solid cybersecurity policy goes a long way. But not everyone in your organization is a security expert. In fact, many employees may not know the first thing about firewalls or viruses—which is why cybersecurity employee training is such a critical matter.

Whether you’re a security leader asked by the board to facilitate a cyber security audit, or a member of the board planning to request one, it’s crucial to know what is a cybersecurity audit & what it isn’t. You need to know precisely what is being asked for to make sure the right information is collected.