Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

We commissioned Forrester Consulting to conduct a 2024 Total Economic Impact™(TEI) Of Bitsight study. Explore research on the financial impact that a typical organization can achieve with Bitsight.

How Bitsight leadership has set up and run a workable AI Council balancing innovation through the use of AI with being a cybersecurity risk management firm.

We dive deeper into a specific area where asset attribution can be particularly nuanced: assessing service providers’ security posture.

This blog follows up with an update on our data engine and the momentum we’re seeing with the second core component: Bitsight Graph of Internet Assets (GIA)
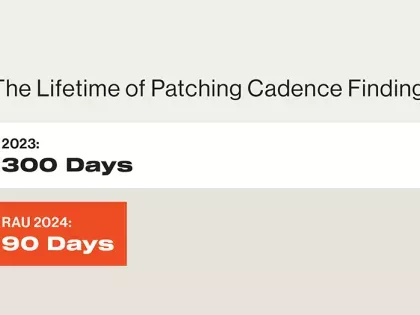
As we announced in January, Bitsight will conduct a ratings algorithm update (RAU) on July 10, 2024, as part of our ongoing efforts to optimize our methodology to provide the best external indicator of the performance of cybersecurity controls.

Vendor Discovery, the latest capability in Bitsight’s Third-Party Risk Management solution, instantly identifies third-party relationships.

The process of removing an association with a CIDR range can be time consuming and frustrating; in light of this, Bitsight has created a program to facilitate and simplify the process.

There is a parallel universe in the cyber world known as the “Dark Web.” It’s a part of the Internet inaccessible via standard browsers or search engines, and it’s where cyber criminals share botnet kits, trade bitcoins, and recruit other hackers to carry out attacks. Over the years, the “Dark Web” has also provided an anonymous marketplace for criminals to sell information stolen from data breaches. An example is from 2015, when nearly 10GBs of data including account details and passwords for some 32 million users of Ashley Madison, were posted on the dark web.

Within the Bitsight Security Ratings platform, we analyze risk vectors specifically chosen to help organizations identify and manage risks across their own networks and the networks of their third parties. Over the past few months, Bitsight has added new risk vectors to enhance the insights across the “spectrum of risk” and provide a more comprehensive picture of an organization’s security posture. These risk vectors will not be factored into our rating calculation until we update and expand the rating algorithm once every year. However, they still provide extremely valuable information to Bitsight users. As new threats emerge, Bitsight understands the important role that these threats play in the security ratings industry. This is why we continuously add to our list of risk vectors — it is critical that security ratings services are dynamic in nature and able to incorporate the identification of these risks into their service.

In the security ratings market, some offerings claim that a staggering percentage of the data they leverage is proprietary, and downplay the value of externally sourced data. While these companies may state that (close to) 100% of their data collection on IP maps, DNS records, event data and more is proprietary, there are several reasons why this is problematic. Let’s break down the myths surrounding this issue one at a time.

In 2014, Bitsight acquired AnubisNetworks, a real-time data threat provider based in Portugal. The integration of AnubisNetworks extends Bitsight’s position as the leading provider of cybersecurity ratings for organizations around the world because it fuels Bitsight Security Ratings’ compromised systems risk vectors and gives Bitsight unparalleled visibility into global threat activity. Anubis’ powerful analytics technology was essential in adding to the scope of Bitsight’s solution that provides daily, continuous security ratings on over 110,000 organizations worldwide.

A new partnership with UP Education Network, a nonprofit school success organization to significantly improve formerly struggling Massachusetts schools.

On February 12, 2013, President Barack Obama issued Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called for collaboration between government and the private sector to create a set of standards for organizations to identify, assess, and manage cybersecurity risk. This led to the NIST Cybersecurity Framework (CSF), a way for organizations to manage cybersecurity risk without the need for additional regulatory requirements. According to the Trends in Security Framework Adoption Survey earlier this year by Tenable Network Security, nearly a third of the organizations they surveyed leverage the NIST Cybersecurity Framework, with many respondents viewing it as an industry best practice.

Cloud computing is not new to the cyber world; it’s here to stay. Web services are common in our everyday lives and workplaces, with things like Facebook, Salesforce, JIRA, Adobe, and GSuite all falling into the cloud-based category. But who is responsible for breaches in the cloud data, the service provider or the organization using their services?
