Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

From the start, it was clear that the Log4j vulnerability, also referred to as Log4Shell, would be widespread and present major challenges for organizations. But, why is addressing Log4j so challenging?
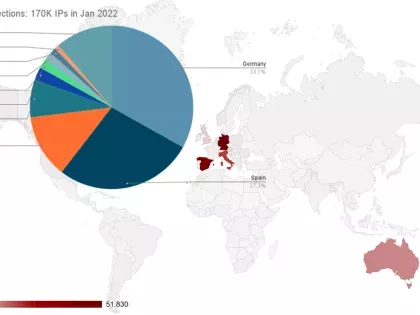
Bitsight has been collecting FluBot infection telemetry data since March 2021. In total, we have identified 1.3 million IPs used by infected Android devices. Of them, over half (61%) are in Germany and Spain. Additionally, we are tracking an increase in IPs over time, which likely indicates an increase in infected devices.

As internet use continues moving toward a mobile-centric experience, it has become essential to consider mobile applications when crafting a security strategy. Bitsight’s latest research demonstrates exactly why. We are excited to announce that Bitsight Insights: Mobile Application Risk Report is available now.

As 2021 comes to a close, we thought it might be a good idea to look back at some of our research from the year. Bitsight investigated a variety of topics including ransomware, vulnerability mitigation, and RSA key generation flaws. We also studied specific vulnerabilities in Microsoft Exchange Server, Apache Server 2.4, and Apache Log4j.

Recent Bitsight research shows that 75% of retail businesses may be at increased risk of ransomware attacks as indicated by poor TLS/SSL configuration management. With the holiday shopping season upon us, it's more important than ever for retailers to evaluate their security posture.
Large retail businesses may have hundreds or even thousands of TLS/SSL certificates identifying specific Internet-connected devices. Plus, many lack an organization-wide framework for discovering, cataloging, and managing TLS/SSL configurations. Instead, management is conducted on an ad hoc basis, usually at a departmental level.
Large retail businesses may have hundreds or even thousands of TLS/SSL certificates identifying specific Internet-connected devices. Plus, many lack an organization-wide framework for discovering, cataloging, and managing TLS/SSL configurations. Instead, management is conducted on an ad hoc basis, usually at a departmental level.

We are excited to announce the availability of the Moody’s Investor Services 2022 Cyber Risk Outlook. The report, which leverages data provided by Bitsight, outlines factors shaping the landscape for cyber risk in 2022. Bitsight is proud to partner with Moody’s on this important research.

Today, the Cybersecurity and Infrastructure Security Agency (CISA) issued Binding Operational Directive (BOD) 22-01, Reducing the Significant Risk of Known Exploited Vulnerabilities, to drive urgent and prioritized remediation of vulnerabilities that are being actively exploited by adversaries.
This directive includes an update to CISA's catalog of “known exploited vulnerabilities,” part of an ongoing effort encourage organizations to reduce risk within their attack surface. Bitsight is proud to partner with CISA on these critical efforts.
In the past few weeks, Bitsight has conducted research on two of the vulnerabilities in the CISA list: CVE-2021-41773 and CVE-2021-42013. These vulnerabilities were introduced via a recent Apache Server update and highlight the importance of an effective software update and patch management strategy as well as the need for third-party risk management.
This directive includes an update to CISA's catalog of “known exploited vulnerabilities,” part of an ongoing effort encourage organizations to reduce risk within their attack surface. Bitsight is proud to partner with CISA on these critical efforts.
In the past few weeks, Bitsight has conducted research on two of the vulnerabilities in the CISA list: CVE-2021-41773 and CVE-2021-42013. These vulnerabilities were introduced via a recent Apache Server update and highlight the importance of an effective software update and patch management strategy as well as the need for third-party risk management.

We are excited to announce a new research partnership with the Cambridge Centre for Risk Studies (CCRS). Our joint research will analyze the relationship between organizational cybersecurity investments and risk reduction.
Bitsight is committed to creating trustworthy, data-driven, and actionable measurements of organizational cybersecurity performance.

A new study published in the Journal of the American Medical Informatics Association (JAMIA) provides brand new perspectives on the state of hospital cybersecurity performance.

Cybersecurity is a critical risk that can materially impact a company’s bottom line. Unfortunately, investors are largely in the dark when it comes to understanding the cybersecurity of the companies in which they invest.

Since 2017 Bitsight has been working together with Microsoft’s Digital Crimes Unit (DCU) to understand the inner workings of the Necurs malware, its botnets and command and control infrastructure in order to take disruptive action against the threat, including reverse engineering, malware analysis, modules updates, infection telemetry and command and control updates and forensic analysis. This week, an action took place to disrupt all Necurs botnets, followed by mitigation and eradication actions.

A few weeks ago Google confirmed that there was malware pre-installed on a number of Android devices due to a supply-chain attack. The latest installment was discovered by security researchers from Dr.Web who have been investigating this situation for several years as it was already theorized by security researchers back in July 2017 that these infections originated as part of a supply-chain attack. In this instance, these devices were pre-installed with Triada, a form of Android malware that has been studied and reported on by Kaspersky and most recently Google in its attempt to surface this critical information to users and the wider community.

On May 14th, Microsoft issued a warning about the BlueKeep vulnerability (CVE-2019-0708) affecting Remote Desktop Services Protocol (RDP), a component common in most versions of Microsoft Windows that allows remote access to its graphical interface. This vulnerability, if exploited by an external attacker, will lead to full system compromise, without requiring any form of authentication or user interaction.

Every day, Bitsight monitors the global threat landscape in a constant effort to identify software that may be placing users and organizations at risk. The presence of malware — or simply potentially unwanted applications — in an organization is an indicator that some security controls may be failing, or that some additional measures should be taken.