Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

On June 9th, a Bitsight team participated in the annual Boston Pride parade for the first time. Boston Pride is a celebration of the city's LGBTQ community and its allies that brings thousands of marchers and spectators into the streets. The parade finishes with a festival at City Hall.
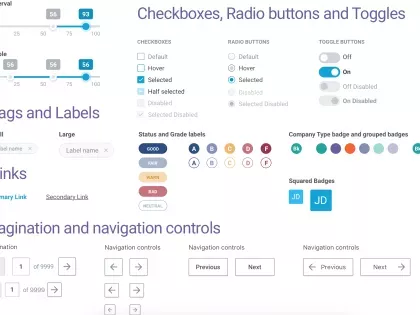
As the Bitsight front end team grows we are investing in our design infrastructure to enable faster development, better collaboration, and a more unified look and feel in our product.
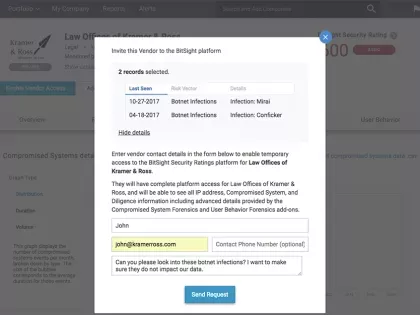
At a recent Bitsight Roadshow, a customer with an advanced third party risk management program declared “assessments are not risk reduction.” The statement was not meant to convey that assessments are useless for third party risk; rather, that assessments themselves don’t inherently drive risk down.

A few months back we added a new feature to the heart of our security ratings portal: the ability for users to not only filter companies in their portfolios, but also to see real-time updated counts of how many "filtered" companies match their selected filter criteria. In practice, this allows users to quickly see, for example, all of their vendors in the Technology or Finance industry with an IP footprint in the U.K or Germany that use Amazon or Google as service providers.
The federal government relies on tens of thousands of contractors and subcontractors — often referred to as the federal “supply chain” — to provide critical services, hold or maintain sensitive data, deliver technology, and perform key functions. Along with the Federal Government itself, these contractors and subcontractors face a multitude of cyber threats.

New Tinynuke variant with a DGA in the wild

Due to security, reliability, and growth reasons, organizations are constantly upgrading their software to newer releases. Some upgrades are incremental and minor in nature. Others, like the upgrade from Django Rest Framework (DRF) V2 to V3, require coding changes due to incompatibilities between the releases. This article is about Bitsight's upgrade experience, lessons learned, and how we improved because of it.

For the second year in a row, Bitsight gave its engineers, product managers, and data and research scientists the day off from normal work to make something cool. The hackathon day had all the typical stuff: awesome custom-designed t-shirts, pizza for lunch, and a demo day the next day. The only “requirement” for teams was that they produce a working prototype to demo. We wanted actual code (not great code, necessarily, but code), not just design mocks.

As 2017 draws to a close, we can’t help but be grateful for what a banner year this has been for Bitsight.

Over 15 years ago, Shaun McConnon, Bitsight’s former CEO and current Executive Chairman of the Board, became involved with giving back to the local Boston community. Shaun and his wife, Bonnie, sat on the Board for a Sudbury-based charity benefitting children with cancer, which was affiliated with the first Proton Beam at Massachusetts General Hospital (MGH).

This October, Bitsight celebrated another very important milestone as the leader and pioneer of the security ratings market: now, Bitsight has high-quality, historical data on over 110,000 global organizations at users’ fingertips.

This August, Bitsight announced the release of several new risk vectors specifically chosen to help organizations identify and manage risks across their own networks and the networks of their third parties. Bitsight chose those new risk vectors to enhance the insights across the “spectrum of risk” and provide a more comprehensive picture of an organization’s security posture.

An increasing number of security and risk management executives are being asked to present to the Board of Directors on the state of their — and their third parties’ — security and risk programs. A recent joint survey by Veracode and NYSE found that nearly 80% of directors said that cybersecurity topics are discussed at nearly every board meeting.

Reducing cyber risk that stems from third and fourth party vendors is no easy task. It requires that organizations not only have the ability to continuously monitor and identify new risk, but also the ability to work with their vendors to fix security issues quickly. Getting to risk reduction quickly means that both organizations are communicating effectively, using data and evidence rather than conjecture to make progress.

When it comes to vendor risk management, organizations ultimately need their vendors to meet the same standard of security performance they hold for their own organization. For years, the Finance industry has been a trailblazer in managing the risk posed by vendors, suppliers, and business partners. However, are vendors in the Finance supply chain meeting the same level of security performance held by Finance organizations?