Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Learn about the four pillars of cyber preparedness and why it’s everyone’s responsibility to get involved.

Learn what you can do to defend against cyber attacks and achieve a state of cyber resilience.

This article contains tips for security and risk professionals to manage risk from their Single Sign-On (SSO) providers and better protect their users’ credentials.

The latest report from Gartner® outlines several key areas that leaders need to pay close attention to if they want to create more resilient, trusted programs.

A vendor security audit can reduce third-party risk. Learn how you can mature your assessment process while saving time and resources.
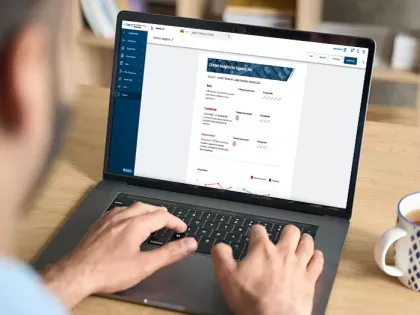
New features in Bitsight's Security Performance Management (SPM) solution help you quickly get better insights of your attack surface so you reduce the risk of data breaches, ransomware, and cyber attacks.
As cyber attacks evolve and your attack surface increases, learn how you can protect your digital perimeter.

Learn what the disturbing ransomware trends means for your organization and third-party vendors.

Rapidly evolving risk and the digitization of banking is creating new threats. Here are three cybersecurity in banking trends to watch this year.

What is information risk management? Learn more about how the classic equation of threat x vulnerability x consequence helps inform your cybersecurity risk management strategy.

The Digital Operational Resilience Act is set to go into action in early 2022. Learn how Bitsight can help your organization meet the compliance requirements.

What does your organization consider an acceptable level of inherent cyber risk in its vendor portfolio? Learn how to establish that threshold and focus resources where they’re needed most.

Learn how to use cyber risk data to protect your organization and its financial assets.

Cybersecurity is a priority for any organization and a big-ticket budget line item. But before investments in security are made, your organization must understand what it is doing right and where improvements to your cybersecurity program are needed.
Typically, this involves conducting a periodic security audit. But these assessments only capture a point-in-time view of the effectiveness of your security controls – and are incredibly resource-intensive.
Typically, this involves conducting a periodic security audit. But these assessments only capture a point-in-time view of the effectiveness of your security controls – and are incredibly resource-intensive.

You can’t reduce the cyber risks faced by your organization if you don’t know what you’re up against. That’s the purpose of a vulnerability probe.