Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

Ransomware isn’t going away; security leaders need to get inside the brain of ransomware sleuths and learn how attacks develop to better identify early indicators of ransomware in their network. Read on to learn how ransomware attacks happen.

Explore actionable attack surface reduction examples that can reduce risk across your expanding digital environment.

Learn what you can do to defend against cyber attacks and achieve a state of cyber resilience.

Join Bitsight at the RSA Conference to learn the latest trends, real-life best practices, and valuable solutions that keep your company protected.

The latest report from Gartner® outlines several key areas that leaders need to pay close attention to if they want to create more resilient, trusted programs.
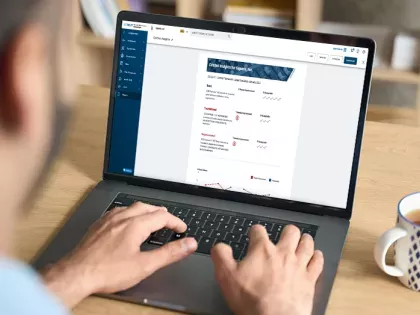
New features in Bitsight's Security Performance Management (SPM) solution help you quickly get better insights of your attack surface so you reduce the risk of data breaches, ransomware, and cyber attacks.
The situation between Russia and Ukraine has been escalating since the start of January, when Russia stationed more than 100,000 troops along the Ukrainian Border. Although cyber security is not the primary concern in the current situation, there is a cyber security component that absolutely should not be overlooked.
We believe a war in the region would have a direct impact on the cyber threat landscape. Both Poland and Lithuania have recently raised their countries' alert level, just hours after Ukraine reported its defense ministry and two banks had been hacked. In the US, CISA has issued a recommendation for all organizations, regardless of size, to adopt a heightened posture when it comes to cybersecurity. Meanwhile, Russia launched a full scale attack on Ukraine territory, which is still developing, and its full reach still remains to be seen.
We believe a war in the region would have a direct impact on the cyber threat landscape. Both Poland and Lithuania have recently raised their countries' alert level, just hours after Ukraine reported its defense ministry and two banks had been hacked. In the US, CISA has issued a recommendation for all organizations, regardless of size, to adopt a heightened posture when it comes to cybersecurity. Meanwhile, Russia launched a full scale attack on Ukraine territory, which is still developing, and its full reach still remains to be seen.
As cyber attacks evolve and your attack surface increases, learn how you can protect your digital perimeter.

Learn how to reduce the threat of cyber intrusion with a detection and prevention approach grounded in continuous monitoring.

The Digital Operational Resilience Act is set to go into action in early 2022. Learn how Bitsight can help your organization meet the compliance requirements.

You can’t reduce the cyber risks faced by your organization if you don’t know what you’re up against. That’s the purpose of a vulnerability probe.

There are many ways that a bad actor can infiltrate your IT infrastructure and begin sifting through your data. These vulnerable entry points are known as risk vectors and include insecure endpoints, unsupported mobile devices, unpatched systems, and more.

Gaps in security controls can be hard to detect. Misconfigured software, open ports, and unpatched systems all expose your organization to cyber risk. They also negatively impact your Bitsight Security Rating.

According to a Cybersecurity Ventures report, global cybercrime costs are expected to grow by 15% per year over the next five years — reaching $10.5 trillion USD annually by 2025. In light of this evolving threat environment and recent widespread security events, today’s cybersecurity leaders are under more pressure than ever to prove that their investments in their programs are actually paying off.

A couple of years ago, industry research firm Gartner introduced a new acronym—SOAR—into the cybersecurity nomenclature. SOAR stands for “security orchestration, automation, and response.” It’s not an individual tool, or even set of tools. Like ISO 27001, GDPR, FISMA, and others, SOAR is a cybersecurity framework organizations can use to create an effective risk mitigation strategy.