Read about the latest cybersecurity news and get advice on third-party vendor risk management, reporting cybersecurity to the Board, managing cyber risks, benchmarking security performance, and more.
Insights blog.

Critical Vulnerabilities Discovered in Automated Tank Gauge Systems
Bitsight TRACE explores several critical vulnerabilities discovered in ATG systems and their inherent risk when exposed to the Internet.

The cybersecurity controls used to manage an organization’s cybersecurity program in previous years will not work against bad actors targeting networks today. Organizations rely more on cloud computing technology, connecting their sensitive data to more third party networks and in turn expanding their attack surface.

Economic pressures push CISOs to justify resources and consolidate tech for data, operational, and cost efficiency. Bitsight aids with comprehensive risk data and solutions.

Let’s look at how you can establish a cybersecurity baseline that works for your unique risks, industry, and business.

As more IT resources shift to cloud service providers, it becomes increasingly complex to get a full digital footprint picture. See how Bitsight helps.
In 2021, ransomware attacks on government agencies globally increased by 1,885% over 2020 attacks, and the trends are continuing so far in 2022. Learn how to protect your organization from ransomware with three best practices.

Attacks targeting operational technology & industrial control systems are rising while many cut security budgets. Comprehensive strategies and monitoring are essential now more than ever.

With economic sanctions being levied by the US against Iran and a trade war heating up with China, some security experts are cautioning that attacks targeting US critical infrastructure may be inevitable. Are electric utilities prepared to defend themselves and their facilities against these attacks?

A chief information security officer (CISO)'s roles and responsibilities include many hats in the realm of cybersecurity — but they are primarily responsible for translating complex business problems into effective information security controls.
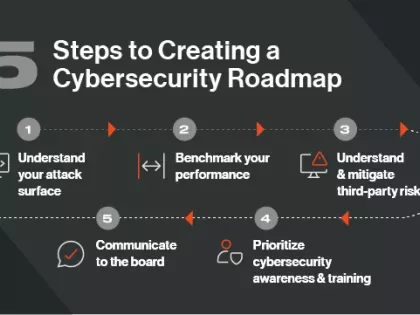
The recent rise in ransomware attacks and business-halting data breaches has made it clear that your organization must prioritize cyber security performance. But ad hoc security controls and defensive measures are not the answer. Instead, you need a strategic, risk-based approach with a cyber security road map as your guide.

Cyber risk mitigation and remediation are often talked about in the same terms. But they are different. Learn how you can optimize both.

Security ratings, or cyber security ratings, are a data-driven, objective and dynamic measurement of an organization’s security performance. Thousands of organizations around the world use Bitsight Security Ratings as a tool to address a variety of critical, interconnected internal and external use cases at scale in order to enable more effective decision making throughout the global business ecosystem.
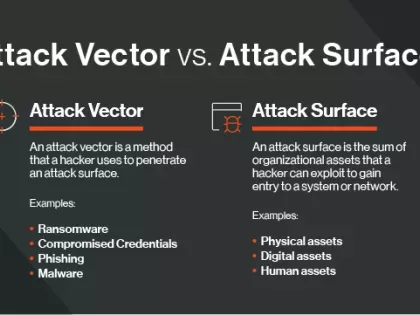
The attack surface encompasses the digital assets that a hacker can exploit. An attack vector is the method they use to breach the attack surface.
Discover how executives and investors are aligning to fortify resilience in the face of evolving cyber threats.

As the world adjusts to more working from home, IT teams worked overtime to enable remote access for millions of employees.

Implementing a cybersecurity incident response plan can help you effectively address a cyber event, reduce disruptions to business, and ensure compliance.