7777 Botnet – Insights into a Multi-Target Botnet

Over the last month there have been some updates about the mysterious 7777 botnet—which was first mentioned in this post in October 2023. Until now, it was known that the botnet was made up of TP-LINK routers and that it was being used to execute very low volume and controlled brute force attacks on Microsoft 365 services targeting corporate accounts. In our continuous efforts to have all sorts of malware families under our radar, the 7777 botnet is no exception. Our research, a collaborative effort between Bitsight TRACE and the security researcher Gi7w0rm, has uncovered additional information about this botnet, the devices it affects, and the victims it claims.
Key Findings About 7777 Botnet
- New cluster of compromised RUCKUS routers
- New cluster of compromised Zyxel firewall appliances
- Discovered a bind shell payload for Axentra devices
- Approximately 16.000 infected devices identified
The Botnet
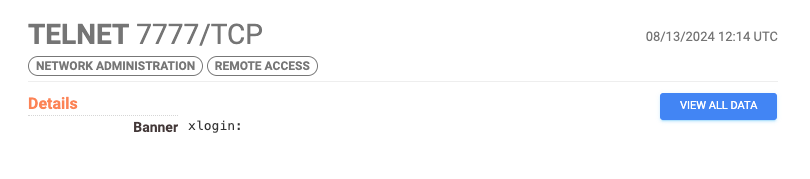
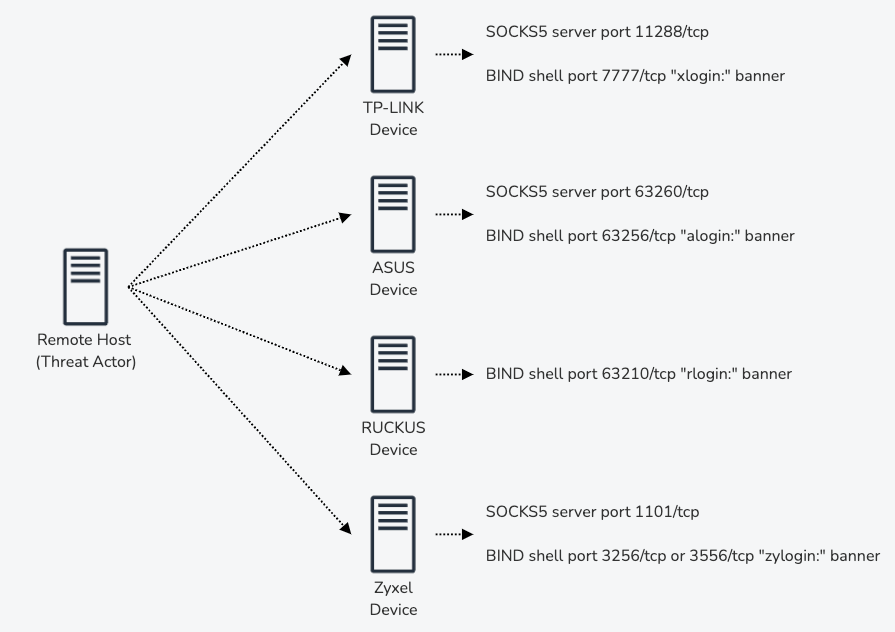
The name 7777 or Quad7 botnet originated from the simple fact that all routers had the port 7777/tcp exposed with the banner xlogin:
In the latest update regarding this botnet, Team Cymru S2 revealed, a new cluster of routers that are also part of this botnet. This new cluster is made up of ASUS routers and all have port 63256/tcp exposed with the banner alogin:

In this blog post, we will reveal two new but smaller clusters of compromised devices that feature bind shells exposing banners very similar to the already known xlogin and alogin banners that are also part of this botnet, and share some up-to-date infection telemetry.
Modus Operandi And New Clusters
After obtaining remote code execution on the devices, the threat actor installs a telnet binary that redirects connections to a bind shell that, after receiving the correct password, opens a new /bin/sh process. In addition to the bind shell that allows the threat actor to maintain direct access to devices, a SOCKS5 server is also installed on the devices so that they can be used as proxies in future brute force attacks.
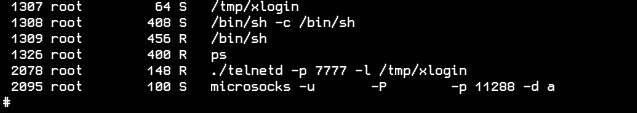
All these artifacts installed on infected devices are placed within the /tmp directory which is volatile in memory. Whenever devices are turned off or restarted, their file system is reset and the contents of the /tmp directory are erased, which causes the threat actor to have to compromise the devices again.
It is worth mentioning that the entry vectors exploited by the threat actor are still unknown to us and trying to obtain this visibility is also not a trivial task as it implies two things:
- have control over an IP that is on the threat actor's target lists
- expose and monitor a vulnerable device, and hope for some luck
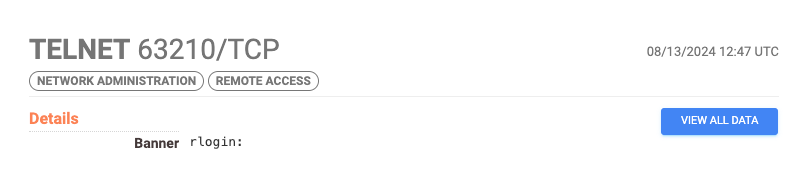
During our investigation we were able to identify two new but smaller clusters of compromised devices that are also part of this botnet. One of these clusters is made up of RUCKUS routers and these devices have port 63210/tcp exposed with the banner rlogin:
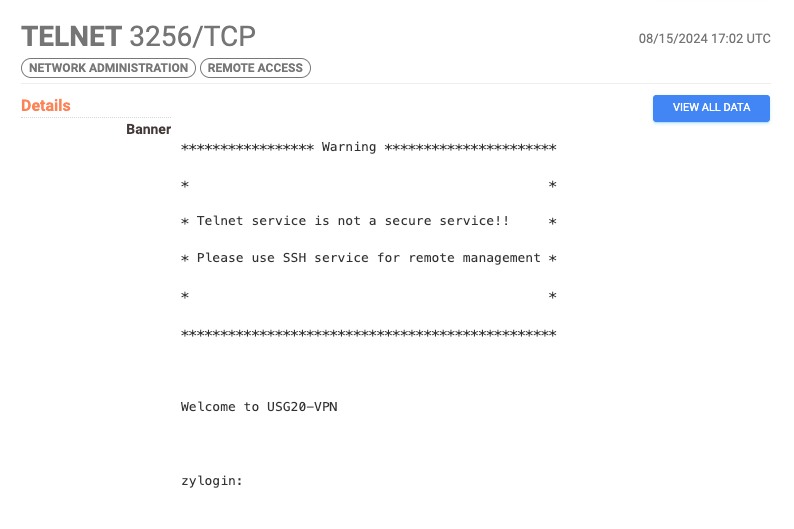
The second cluster is even smaller and is made up of compromised Zyxel Firewall appliances. These devices have either port 3256/tcp or port 3556/tcp exposed with the banner zylogin:
In the image below you can see what happens to the devices in the case of a successful exploitation attempt.
Axentra bind shell
We found an additional bind shell binary belonging to this threat actor's tooling that exposes the axlogin: banner.
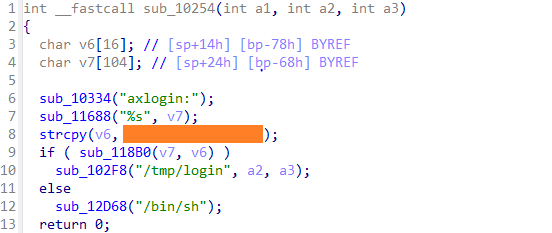
We confirmed that this bind shell was used to backdoor Axentra devices, although no devices were found displaying this banner, likely because the company and its products have been discontinued for a long time now.
Victims
Based on available data, it is estimated that the botnet may have compromised more than 175.000 devices since it began operating. During the last 30 days, through our internet scans, we were able to identify a total of around 16.000 infected devices with exposed bind shells. The fact that all infections are ephemeral, ie. require re-exploitation whenever a device is turned off or restarted, and that only about 9% of the devices remain infected to this day could be seen as an indicator that the threat actor has not been updating its targets for some time now. Still, we are looking at a decent sized and low profile botnet that has allowed the threat actor to conduct various brute force attacks to this day.
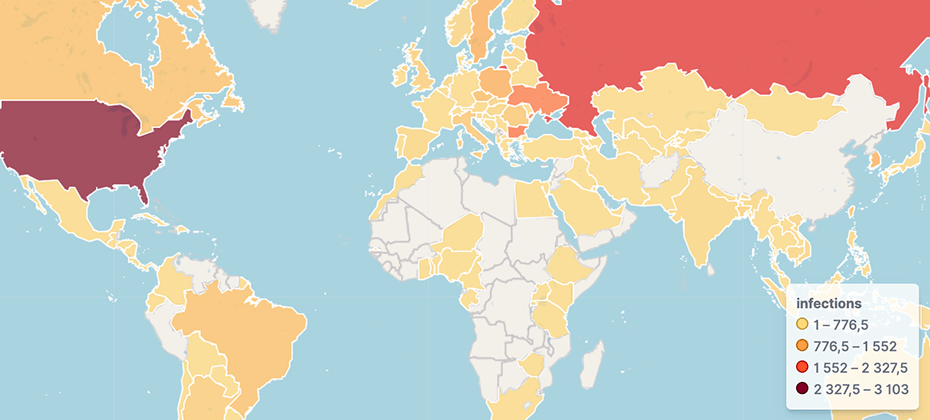
The top 5 countries with the highest number of compromised devices are in order:
- US (3103 devices)
- RU (2109 devices)
- BG (1390 devices)
- UA (1286 devices)
- PL (689 devices)
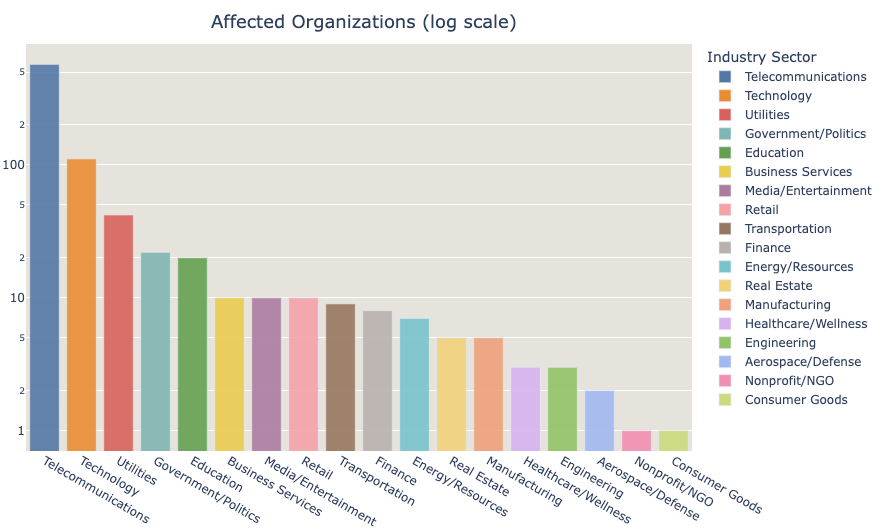
As a botnet that is essentially targeting consumer devices such as routers, the expectation is that it would mostly affect residential users. Although the majority of cases align with our expectations, it is quite interesting to note that of the 840 organizations that we identified with at least one infected device, approximately 20% are not Internet Service Providers (ISPs). It is quite concerning to also see that there are infected devices belonging to Government institutions, many of them present in the USA.
7777 cluster victims
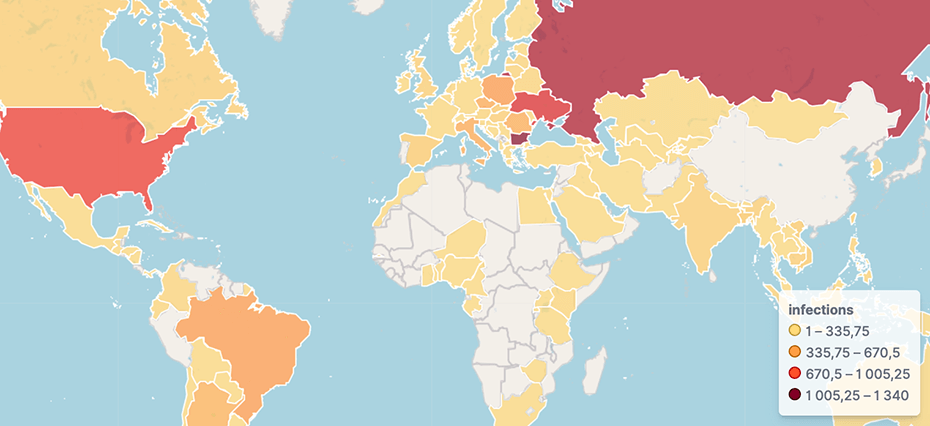
The 7777 cluster of TP-LINK routers has around 8.303 infected devices and the top 5 affected countries remain the same, although the order changes.:
- BG (1340 devices)
- RU (1192 devices)
- UA (967 devices)
- US (829 devices)
- PL (410 devices)
63256 cluster victims
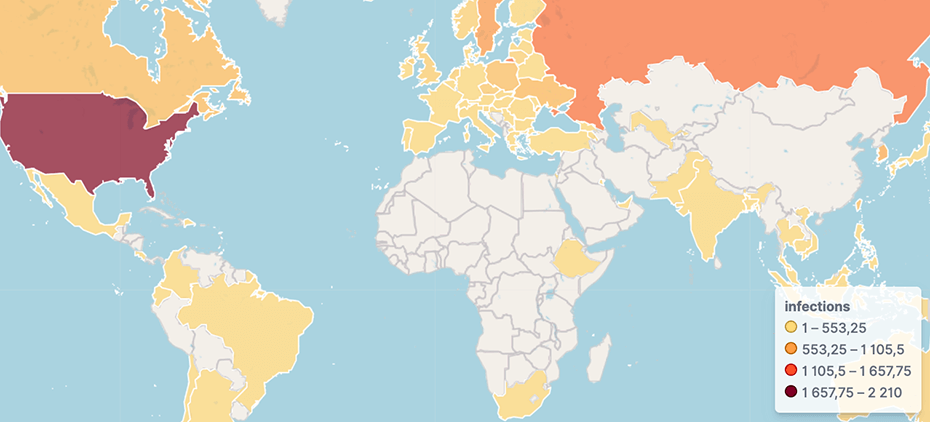
The 63256 cluster of ASUS routers has around 7.192 infected devices and here the top 5 affected countries already change a little:
- US (2210 devices)
- RU (917 devices)
- SE (625 devices)
- KR (471 devices)
- HK (406 devices)
63210 cluster victims
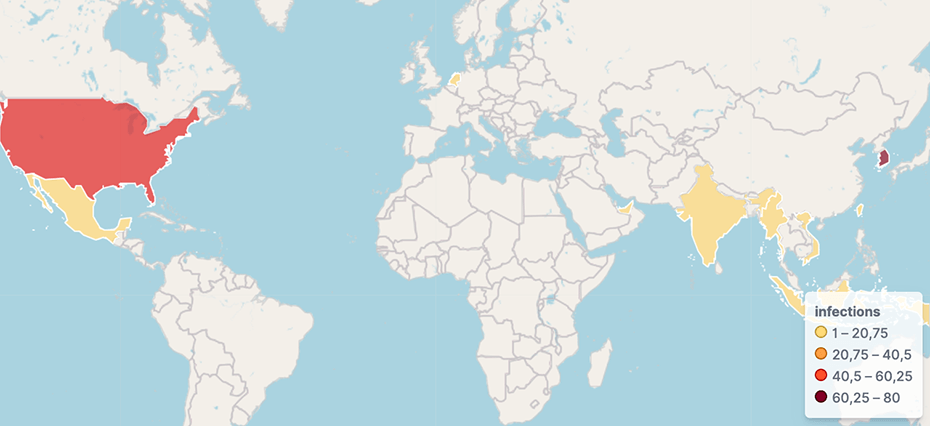
The 63210 cluster of RUCKUS routers has less than 200 infected devices and the top 3 affected countries are:
- KR (80 devices)
- US (56 devices)
- TW (5 devices)
3256/3556 cluster victims
This cluster of compromised Zyxel devices is particularly interesting because only a total of 4 compromised hosts have been identified, all located in Hong Kong.
Targeted Device Models
During our investigation of this botnet, we were able to identify a very significant number of device models that have been compromised. The diversity of affected models highlights the good capacity that this threat actor has to exploit vulnerabilities, which leads us to believe that this botnet could be part of an operation with good resources and capable of targeting devices of various brands and models.
The following models were found to be compromised:
| ASUS | TP-LINK | Zyxel | RUCKUS |
|---|---|---|---|
|
|
|
|
Wrap-Up
There is some speculation regarding the purpose of this botnet and whether its activity is related to the interests of a particular state. At the moment, the only certainty that exists is that the botnet is being used to attack corporate accounts of interest through brute force attacks on Microsoft 365 services, always at a very low volume, in order to maintain a low profile and avoid detection.
There are some indicators publicly shared by the research community that suggest this botnet is likely operated by a threat actor originating from China. We were able to deeply investigate some of the infrastructure related to this botnet and, based on the evidence collected, we are very confident that this botnet is operated by a Chinese speaking threat actor.
We will continue to monitor the evolution of this botnet. If you are researching it and want to collaborate/exchange notes feel free to contact us at [email protected].
